Share this
Automatically Logging PowerShell in to Azure
by Adam Knight on 19 September 2017
This article is republished from my original Automatically Logging PowerShell in to Azure post on fantail.io.
I've been working with Azure Resource Manager templates a lot lately, as an easy, repeatable way to create deployment environments for my code. ARM templates are a JSON description of a resource or grouping of resources and can be applied to create or update an environment. This means you can roll out a new environment quickly and easily - perfect for quickly setting up a Dev or Test system, and you know that if you use the same templates to configure Production you won't have any surprises, or "Well, it worked in Dev..." conversations.
The best thing about ARM templates for me is how easy it is to generate them. If you have a resource group, you can create a template by clicking on the Automation Script button:
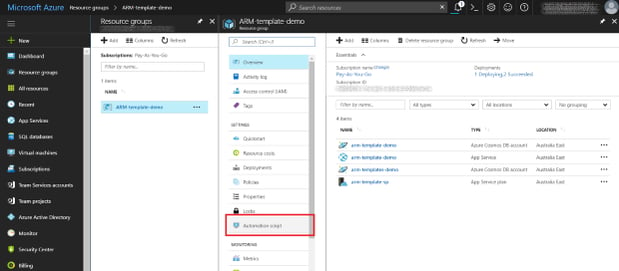
This will create a show you a JSON template and supporting files that can be downloaded as a Zip. It contains all the information needed to reproduce your resource group's infrastructure. It isn't a backup though - it doesn't have the website code or the rows from your database or anything. My automation script view looks like this:
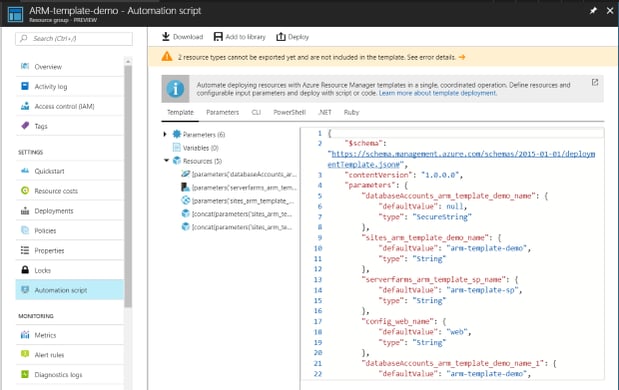
The template is a little rough around the edges - the parameter names are very tightly tied to the original resource group ("databaseAccounts_arm_template_demo_name" for example) but will work almost straight away. The zip file contains the following files:
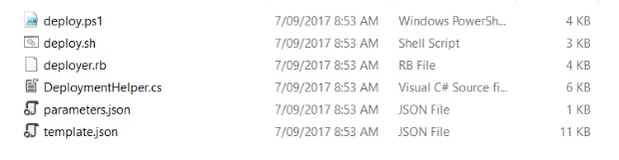
The template and parameters files go together - the parameter file contains the various settings that can be changed for each deployment or environment. You can copy this file for different deploys, changing the web server to a more powerful type in Production or whatever. Out of the box all values are set to null, though - you need to change this before the template will work. Alternatively, delete the parameters file as the template has defaults that will be used instead.
My parameters file is above - replace all the nulls with the appropriate values (use the template's default values as guides), and you can try a deployment. Open PowerShell and run deploy.ps1:
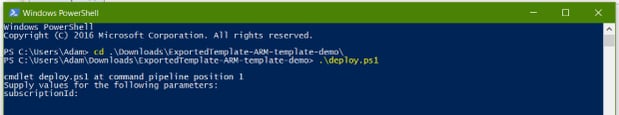
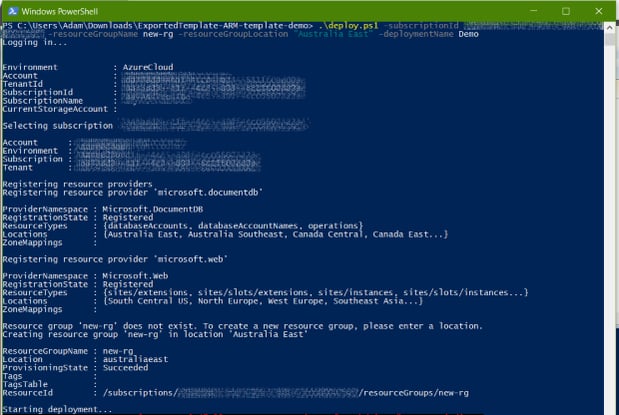
The script asks for your subscription ID, and the resource group name you want to deploy to, then it opens an Azure login dialogue. This is OK at first, but gets really tiresome after a while, especially if you're trying out different parameters and settings like I was. Fortunately it's easy to fix.
All of the parameters for the PowerShell script are described at the beginning of the file - you can set these on the command line so you don't have to type them in again and again:
This is much easier to run and re-run but it still makes you log in every time. The answer to this is using a Service Principal to connect and run the deploy, rather than logging in yourself. The Service Principal can be set up to use a certificate to authenticate, meaning you don't need to supply a key or password each time. Service Principals are explained here, and if you're from a Unix background like me you can think of them as the user that an application runs as. When you run Apache or PostgreSQL on a server, for example, they don't run as root but as some other user so that if they're breached, the hacker does not have root access. Instead they'll get "apache" or "postgres" user permissions which are usually very limited.
In practice I have found adding Service Principals via the Azure Portal quite tricky. Part of this is working out where to grant access, and another part is the various IDs that Microsoft make you use (ObjectId, ApplicationId, ClientId...) and trying to work out whether the ApplicationId or the ObjectId is ClientId (no seriously, Microsoft! What are you thinking!?) Fortunately I found some PowerShell to create a Service Principal and configure it:
This script makes you log in to the Azure account, and creates a Service Principal for you. It does get Contributor access to your subscription, so this may not be for you - I will look at limiting its access to a single resource group in future. Contributors have the ability to alter any resource in their scope, but can't assign other people this right - so if someone cracks your Contributor access they can delete all your resources! Be careful, this may not be right for you.
Once you've run this script, check in your Active Directory for the new Application Registration (related to the Service Principal):
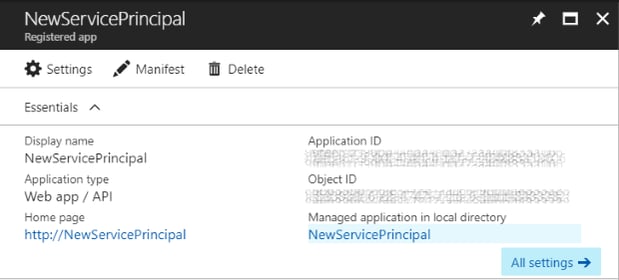
You're ready to test out the easy login now. Take note of the ApplicationID of the Service Principal, and the TenantId (the ID of your Azure Active Directory) then run this PowerShell:
$Thumbprint = (Get-ChildItem cert:\CurrentUser\My\ | Where-Object {$_.Subject -match "NewServicePrincipal" }).Thumbprint
Login-AzureRmAccount -ServicePrincipal -CertificateThumbprint $Thumbprint -ApplicationId <App ID> -TenantId <Tenant ID>
This will look up the "NewServicePrincipal" certificate in your keychain, and use this to authenticate to Azure. It will log in and has Contributor rights, so can alter resources for you. Perfect!
All that's left to do now is to modify the deploy.ps1 script so that it uses this login:
I added 3 parameters to the beginning (applicationId, tenantId and certificateSubject) and modified the lines around the login.
The deploy script will now log in automatically and not prompt for any parameters - the final PowerShell command looks like this:deploy.ps1 -subscriptionId <Subscription ID> -resourceGroupName new-rg -resourceGroupLocation "Australia East" -deploymentName Demo -applicationId <App ID> -tenantId <Tenant ID> -certificateSubject NewServicePrincipal
Hope this helps speed up your ARM template development!
Adam Knight is an Auckland-based Senior Solution Architect in Equinox IT's Cloud business.
Share this
- Agile Development (153)
- Software Development (126)
- Agile (76)
- Scrum (66)
- Application Lifecycle Management (50)
- Capability Development (47)
- Business Analysis (46)
- DevOps (43)
- IT Professional (42)
- Equinox IT News (41)
- Agile Transformation (38)
- IT Consulting (38)
- Knowledge Sharing (36)
- Lean Software Development (35)
- Requirements (35)
- Strategic Planning (35)
- Solution Architecture (34)
- Digital Disruption (32)
- IT Project (31)
- International Leaders (31)
- Cloud (26)
- Digital Transformation (26)
- Project Management (26)
- Azure DevOps (23)
- Coaching (23)
- IT Governance (23)
- System Performance (23)
- Innovation (21)
- Change Management (20)
- MIT Sloan CISR (15)
- Client Briefing Events (13)
- Architecture (12)
- Working from Home (12)
- IT Services (10)
- Data Visualisation (9)
- Kanban (9)
- People (9)
- Business Architecture (8)
- Communities of Practice (8)
- Continuous Integration (7)
- Business Case (4)
- Enterprise Analysis (4)
- Angular UIs (3)
- Business Rules (3)
- GitHub (3)
- Java Development (3)
- Lean Startup (3)
- Satir Change Model (3)
- AI (2)
- API (2)
- Automation (2)
- Scaling (2)
- Security (2)
- Toggles (2)
- ✨ (2)
- .Net Core (1)
- Diversity (1)
- Microsoft Azure (1)
- Testing (1)
- December 2024 (1)
- August 2024 (1)
- February 2024 (3)
- January 2024 (1)
- September 2023 (2)
- July 2023 (3)
- August 2022 (4)
- August 2021 (1)
- July 2021 (1)
- June 2021 (1)
- May 2021 (1)
- March 2021 (1)
- February 2021 (2)
- November 2020 (2)
- September 2020 (1)
- July 2020 (1)
- June 2020 (3)
- May 2020 (3)
- April 2020 (2)
- March 2020 (8)
- February 2020 (1)
- November 2019 (1)
- August 2019 (1)
- July 2019 (2)
- June 2019 (2)
- April 2019 (3)
- March 2019 (2)
- February 2019 (1)
- December 2018 (3)
- November 2018 (3)
- October 2018 (3)
- September 2018 (1)
- August 2018 (4)
- July 2018 (5)
- June 2018 (1)
- May 2018 (1)
- April 2018 (5)
- March 2018 (3)
- February 2018 (2)
- January 2018 (2)
- December 2017 (2)
- November 2017 (3)
- October 2017 (4)
- September 2017 (5)
- August 2017 (3)
- July 2017 (3)
- June 2017 (1)
- May 2017 (1)
- March 2017 (1)
- February 2017 (3)
- January 2017 (1)
- November 2016 (1)
- October 2016 (6)
- September 2016 (1)
- August 2016 (5)
- July 2016 (3)
- June 2016 (4)
- May 2016 (7)
- April 2016 (13)
- March 2016 (8)
- February 2016 (8)
- January 2016 (7)
- December 2015 (9)
- November 2015 (12)
- October 2015 (4)
- September 2015 (2)
- August 2015 (3)
- July 2015 (8)
- June 2015 (7)
- April 2015 (2)
- March 2015 (3)
- February 2015 (2)
- December 2014 (4)
- September 2014 (2)
- July 2014 (1)
- June 2014 (2)
- May 2014 (9)
- April 2014 (1)
- March 2014 (2)
- February 2014 (2)
- December 2013 (1)
- November 2013 (2)
- October 2013 (3)
- September 2013 (2)
- August 2013 (6)
- July 2013 (2)
- June 2013 (1)
- May 2013 (4)
- April 2013 (5)
- March 2013 (2)
- February 2013 (2)
- January 2013 (2)
- December 2012 (1)
- November 2012 (1)
- October 2012 (2)
- September 2012 (3)
- August 2012 (3)
- July 2012 (3)
- June 2012 (1)
- May 2012 (1)
- April 2012 (1)
- February 2012 (1)
- December 2011 (4)
- November 2011 (2)
- October 2011 (2)
- September 2011 (4)
- August 2011 (2)
- July 2011 (3)
- June 2011 (4)
- May 2011 (2)
- April 2011 (2)
- March 2011 (3)
- February 2011 (1)
- January 2011 (4)
- December 2010 (2)
- November 2010 (3)
- October 2010 (1)
- September 2010 (1)
- May 2010 (1)
- February 2010 (1)
- July 2009 (1)
- April 2009 (1)
- October 2008 (1)